RSA6.1
Surface-mount Zener and TVS diodes for circuit protection
Manufacturer: rohm
series introduction
# Introduction to the RSA6.1 Product Series
## Overview
The RSA6.1 product series represents a significant leap forward in technological innovation, designed to meet the diverse and complex needs of modern industries. Whether it's in the realm of data security, network management, or advanced analytics, RSA6.1 offers a comprehensive suite of solutions that combine cutting - edge technology with user - friendly interfaces.
## Key Features
### 1. Advanced Encryption Algorithms
At the heart of the RSA6.1 series lies its state - of - the - art encryption algorithms. These algorithms are based on the latest research in cryptography, providing a high level of security for sensitive data. RSA6.1 uses a combination of symmetric and asymmetric encryption techniques, ensuring that data is protected both at rest and in transit. For example, it can encrypt large volumes of data stored in data centers with AES (Advanced Encryption Standard) for fast and efficient processing, while using RSA public - key cryptography for secure key exchange and digital signatures. This dual - approach not only enhances security but also provides flexibility in different security scenarios.
### 2. Scalability
One of the standout features of the RSA6.1 series is its scalability. Whether you are a small - to - medium - sized business or a large enterprise, the RSA6.1 products can be easily scaled to meet your growing needs. The hardware components are modular, allowing for easy addition of processing power, storage, and network interfaces. In a software - defined environment, the RSA6.1 software can be deployed across multiple servers and virtual machines, enabling seamless expansion as your data and user base grow. This scalability ensures that you can invest in the RSA6.1 series with confidence, knowing that it can adapt to your changing business requirements.
### 3. Real - Time Analytics
RSA6.1 comes equipped with powerful real - time analytics capabilities. It can collect, process, and analyze large amounts of data from various sources, such as network traffic, user behavior, and system logs, in real - time. This allows organizations to detect and respond to security threats, performance issues, and other critical events immediately. For instance, the analytics engine can identify patterns of abnormal network traffic that may indicate a cyber - attack, and trigger automated responses such as blocking the suspicious IP addresses or alerting the security team. The real - time analytics also provide valuable insights into business operations, helping organizations optimize their processes and improve efficiency.
### 4. User - Friendly Interface
Despite its advanced technical capabilities, the RSA6.1 series features a user - friendly interface. The graphical user interface (GUI) is intuitive and easy to navigate, even for non - technical users. It provides a centralized dashboard where users can monitor system status, configure settings, and view reports. The interface also includes wizards and templates that simplify complex tasks, such as setting up encryption policies or configuring network security rules. This user - centric design ensures that organizations can quickly adopt and utilize the RSA6.1 products without extensive training.
## Product Variants
### 1. RSA6.1 Data Security Appliance
This variant is specifically designed for data security. It can be deployed at the edge of a network or within a data center to protect sensitive data from unauthorized access. The appliance includes features such as data encryption, access control, and data loss prevention. It can also integrate with existing security infrastructure, such as firewalls and intrusion detection systems, to provide a comprehensive security solution.
### 2. RSA6.1 Network Management System
The network management system in the RSA6.1 series is used to monitor and manage network devices and traffic. It provides real - time visibility into network performance, including bandwidth utilization, latency, and packet loss. The system can also automate network configuration tasks, such as device provisioning and policy enforcement. This helps organizations optimize their network resources and ensure reliable network
Images for reference

RSA6.1 Series Pin Out

SOT25
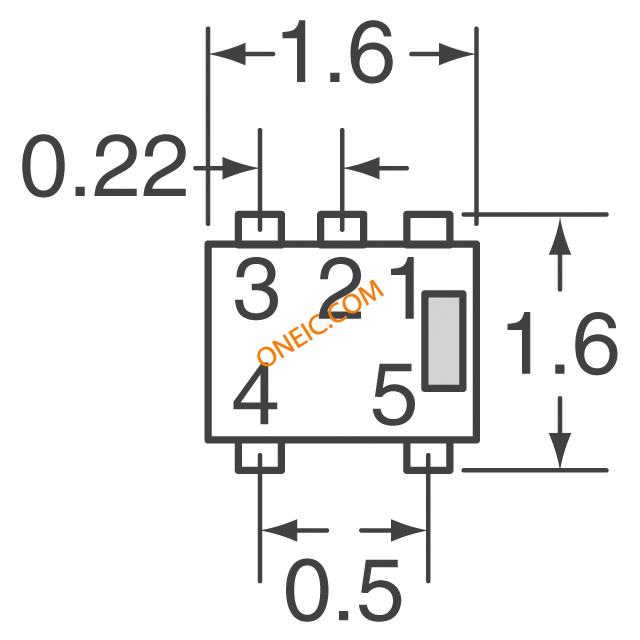
RSA6.1 Series Pin Out